Ultius Blog
How Network Security Impacts Essay Writing Services
Network security is a complicated and multi-faceted topic that was once only discussed by IT experts. However, with the expansion of ‘wi-fi’ across the country and the globe; a comprehensive understanding of the topic is a necessary prerequisite for secure access of the internet at home, school, and work. There are a variety of resources available that provide a series of best practice suggestions applicable across the spectrum of industries and organizations of different sizes and missions.
Network security is not an issue to be grappled with by one industry (be it retail, government, manufacturing, or writings services) but is a shared concern. Therefore, this post will iterate and decipher research-based best practices for network security according to diverse sources.
As the reader will come to understand:
- Why online security is everyone’s business
- The role network security plays in the writing service industry
- The steps all businesses need to take to keep customers safe online
- What you can do to keep yourself safe online
- How to identify secure writing services and websites
Network security: a shared concern of every business (including writing services)
There is a wealth of research and academic journal articles specific to the subject of best practices in network security for multiple environments – both personal and professional.
One recent study undertook to examine the manner in which small businesses and enterprises of fewer than 500 employees are executing their comprehensive information security needs and risks.
Today’s small businesses find they are now better able to compete more effectively with larger companies than ever before due to the expanding geographical scope offered by Internet access. However, “this adoption of new technology whereby a broadband connection is always ‘on’ has introduced unexpected security threats to small businesses for which they may lack the monetary resources and expertise to address effectively” (Keller, Powell, Horstmann, Predmore, & Crawford).
In this instance, the network administrators or information security officers of eighteen companies in a large Midwestern city participated in an face-to-face interview where they were asked about their expertise in threat perception and awareness of professionally identified “best practices in securing organizational information that includes (but is not limited to) firewall installation; protections against worms, holes and Trojans; stringent password policies and physical security measures; identity services and remote usage policies” (Keller et al.).
Studies show online security is everyone’s business
A similar article parrots some of the propositions of this initial study. In this case the author emphasizes that the “most valuable option to be pursued in network security is to develop a thorough, comprehensive top-down policy that begins when the decision maker be able to define what it is they are trying to protect and what they need to protect against” (Wilson).
The writer reiterates a point that will be addressed several times throughout this post and that is that in today’s environment network security is everybody’s business and that is a best practice cornerstone on which to base any and all policy development. Moreover, this policy creation requires preparation, organization, and execution to evaluate the credibility of a website. To be sure, policy development forms the basis from which all network security best practices are able to be implemented. Network security is in the best interest of everyone, especially essay writing services.
Are essay writing services safe?
Network security is the responsibly of every business with an online presence. The majority of online writing services are small business websites. Which begs the question, is buying an essay online safe?
The short answer is “it depends.” The long answer is there are many essay writing services that are safe and trustworthy with success stories as evidence. However, some essay writing services are more trustworthy than others and it’s not uncommon to into two problems:
- Be a victim of a scam by an untrustworthy essay writing service.
- Find a trustworthy writing service with unsafe security practices.
Confidentiality is one of the biggest concerns for many students who choose to buy essays online. Students should feel safe using writing services to assist them in the learning process whether it’s for editing or for a custom sample paper. Compromised and exposed confidential information can make or break a student’s academic career. This is the reason online writing services, like any other business, need protect their clients’ personal information.
At Ultius, we use third-party vendors to process payment information when clients place an order. This measure ensures our clients’ personal identifying information is not disclosed to anyone (including their writer) or linked to the subject matter of their order. It also helps to ensure their payment details and financial information are securely and privately protected.
A safe and trustworthy writing service will make sure their client’s security is protected. Essay writing services, along with other online businesses, need to constantly keep up with new threats to cyber security and have a plan in place to keep their customers safe.
Threats in network security
Today, companies are facing new types of threats that affect individual computers, individual and multiple networks, and even regional networks. Worms are increasingly popular over viruses and can self-replicate to quickly infect a large number of users. Of increasing concern is the expansion of spyware, adware, and malware.
These programs are downloaded to machines without the knowledge or the consent of the user; simply by visiting websites, these programs can be downloaded to a user's computer without the user being aware that a program was installed. It’s possible to visit an unsafe site of an essay writing service and have harmful programs downloaded to your computer without your consent. Pro tip: before you visit a website look for these red flags using review services.
In a more recent article from a peer-reviewed journal the author provides a series of ten best practice security recommendations for protecting personal identifiable data; all are sensible and cost-effective to the individual and/or organization. The list of precautions includes:
- knowing your data and its flow and usage,
- encrypt, regulate and educate,
- unify and streamline processes,
- run regular audits,
- ensure physical security (such as not leaving your computer unattended with sensitive information showing),
- devise a value-based data retention policy (Rapkin).
Arguably, the most valuable piece of advice the writer offers is to devise a value-based data retention policy; which means to be mindful of the fact that the more data an organization or individual stores, the greater there is to protect. However, this data should be regularly analyzed to ensure it continues to be of value and cost-effective in terms of reward versus risk. Keep data retention policies current.
According to another researcher there is simply nothing easy about network security and therein lies the problem. This study states “there are a variety of best practices that can keep most businesses safe from the most likely and pervasive threats, but more than half of all IT departments are failing at some of the most important security practices” (National Institute of Standards and Technology 2011).
The culprit seems to the failure on behalf of many companies to use appropriately strong encryption keys. Among the recommendations they offer are regular training of staff in the latest network security of best practices – particularly in light of the increased presence of cloud computing - and having a plan in place to immediately address and replace breaches.
In light of this; it is not frivolous to note that from all appearances it is a constant effort to stay one step ahead of hackers. In the writing service industry, knowing how to avoid online writing scams goes hand-in-hand with online security.
What to look for in a secure writing service
The research shows many companies fail to use appropriate encryption keys. But, how can customers ensure a writing service is taking the necessary precautions? Researchers propose regular training, but its not like customers can join writers or the support team for regularly scheduled security meetings. So, how can a customer find an essay writing service that’s trustworthy? How can customers be sure an essay writing service has top-tier security?
There are a few pieces of information one can look for on an essay writing website to determine whether or not the website is up to date on their online security standards. Look for:
- basic security validation,
- extended security validation,
- and third-party security vendors.
Basic security validation
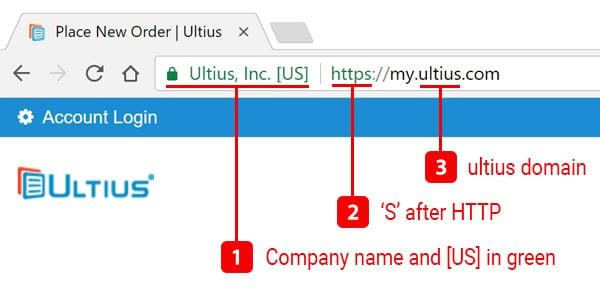
Websites with verified security are safer and more trustworthy than sites that don’t have verified security. Basic security validation is the entry-level requirement of online security and if any website, specially a business website, doesn’t have it, it’s best to avoid it altogether.
The basic security certificate can be found before the URL, and it can easily be identified as a lock or with the word “Secure.” If you click on it in a Google Chrome browser, a message will pop up reading; “Connection is secure.” As of 2019, Mozilla Firefox and Microsoft Edge both use a similar lock symbol on the top left of the browser next to the URL bar.
Extended security validation
An extended validation certificate is used for “https” websites to prove the legal entity of the owner and is considered to be the highest level of trust a company can display for its visitors. Simply check the if URL of the website begins with "http" or "https." The "s" in the “https” stands for “secure” meaning all data transferred to the site will be encrypted protecting information from hackers who may attempt to access it.
Third-party security vendors
Past the initial certificate verification, you can also explore the sites themselves to determine what kinds of additional security they have taken to protect visitors and customers. You can bet if an essay writing service has additional security, they will advertise it on the website.
It’s important to click through a few pages to look information about additional security. If you can’t find additional information about security, then the writing service probably doesn’t have it. For example, Ultius has a whole slew of protections to ensure the website security and the confidentiality of customer information. We offer security tips to help keep your data secure, not just on our site, but everywhere else online.
Here’s a list of top-tier, third-part vendors:
- Armor: a hosting provider focused on security
- Cisco: provides internal server two-factor authentication
- CloudFlare: manages website traffic and filters out suspicious characters
- GeoTrust: issues SSL certificates; provides 256-bit encryptions
- Google Apps for Work: used to secure internal company communication
- McAfee Secure: scans websites for malicious code (easily identifiable by its trust seal)
Security awareness across an organization
And, related to the subject of network security standards and best practices is the concern for the level of security awareness across an organization. According to one comprehensive study “recent global security surveys indicate that security training and awareness programs are not working as well as they could be and that investments made by organizations are inadequate” (Tsohou, Karyda, Kokolakis, & Kiountouzis 2012). The authors’ purpose was to increase understanding of this problem; and to urge companies as well to establish an information security awareness program.
While this study may present a much more sophisticated level of information regarding network security and best practices; the point is reiterated that there seems to be an overall lack of understanding about network security.
Other findings include the fact that “information security awareness initiatives involve different stakeholders, with often conflicting interests” (ibid) Practitioners must acquire a breadth of skills and issues and as this research connotes – may not be ‘neutral’ in its application.
This demands a reengineering of the totality of governmental processes related to online service as well as reframing of the legalities related to such. In this case, the researchers conclude that the process begins with educating the public while restructuring the architectural scaffold that implements and delivers the breadth of organizational services; ensuring that the government is sensitive to the needs of the end-users while guaranteeing best-practice network security.
The final research we will address in this post explains the reason for the study this way. “All forms of modern organizations, whether they are operating in the public or the private sector, have become far more dependent upon a wide range of information technologies to support all aspects of their strategic and operational activities that may have the potential to deliver important benefits but are compromised because of the unacceptably high levels of security breaches experienced” (Garg, Curtis, Halper 2003).
Adopting an acceptable use policy
As time goes on it is becoming increasingly apparent that the “weak link in network security is the user who can be seen to manipulate the computer and network in an inappropriate or insecure manner” (Schneir 2000) which ultimately places the employer at risk of information and financial loss and – increasingly – litigation and/or prosecution. Universities, private entities and the government itself are all at risk of these outcomes. A valuable defensive response to this is for these organizations to have an ironclad ‘acceptable use policy (AUP) to protect the integrity and accuracy of these resources.
The aim of the study; then, “is to fill this gap in the literature by critically examining the structure and composition of a sample of authentic policies” (Dohertya, Anastasakisa, & Fulford 2011). Of all of the research; this is the most extensive in terms of data analysis and manageable conclusions. While the focus of the research was on the environment of higher education; certainly, there are lessons that are applicable across the spectrum of network users.
The best practical use of AUP, according to the writers, may be the best front-line defense in preventing breaches. Their findings include that universities must acknowledge that “the primary role of the AUP is as a mechanism for addressing unacceptable behavior and not as a proactive tool for promoting desirable and effective security behaviors; and due to the realization uncovered by this study that there is a wide variation in the coverage and positioning of the reviewed policies” (Dohertya, Anastasakisa, & Fulford 2011). More importantly, however, is the need for organizations to acknowledge that a ‘cookie cutter’ policy is unlikely to foster comprehensive network security.
Network security moving forward
The spread of internet access requires a change in the standards of its usage to ensure optimum safety at home, school, or work. As one author noted “there is a rich repertoire of standards and best practices on the system and info-security landscape; because as technology evolves the security situation becomes more complex” (Kizza 2005). It now behooves all network users to become competent and cautious when accessing the internet.
In this case, the best offense is a good defense; in other words, it is imperative to have a sound and comprehensive security strategy that stays abreast of the sphere of changes in technology. As a customer looking for an essay writing service, being vigilant of a website’s security features is the number one strategy.
As this review of the literature reveals, network security is the issue of public and private entities alike; and a wealth of recommendations are currently available from an equally expansive array of studies and reports. Included among them (and mentioned repeatedly) are the simple suggestions to educate the user on what is considered ‘acceptable use’ by the organization as well as training in the simple art of proper keywording; encryption and safeguarding equipment. For example, an essay writing service not communicating their security features with their customer and web visitors may not be safe or trustworthy.
Finally, network management requires the conscious revisiting of the issues of management, planning, policy development and design procedures. Unfortunately, network security cannot lie solely with the ‘expert’ who has been employed by an organization for the specific purpose of implementing network best practices. Now, and going forward, each individual will be required to bear a greater personal responsibility for the knowledgeable acquisition and application of safety standards.
Find a safe writing service you trust
Today, finding a website you can trust, especially to do business with can be difficult. Network security is everyone’s responsibility. In this industry, essay writing services need to be transparent about the measures they sure to keep their customers safe. Customers need to take extra precaution and look for signs on the website to signaling safety and trust.
At Ultius, we make your safety our priority. We obtained extended validation SSL certificates from GeoTrust, which is not a quick and easy process. There are several steps that must be taken and verified before a company can receive their certificate. GeoTrust must be able to verify a company’s registration with a governmental agency, and an entire host of other criteria.
Our website is McAfee Secure and scanned daily for malicious code and other cyber threats as an extra layer of security beyond our security certificate. You can find the McAfee Secure seal throughout our site.
No matter what website you visit, look for one that prioritizes keeping your private information safe. Look for an essay writing service that puts your security first, and you’ll be on your way to success!
References
Dohertya, N.; Anastasakisa, L.; Fulford, H. (2011). Reinforcing the security of corporate information resources: A critical review of the role of the acceptable use policy. International Journal of Information Management; Vol 31, Iss 3; pp. 201–209.
Garg, A.; Curtis, J.; Halper, H. (2003). Quantifying the financial impact of information security breaches. Information Management and Computer Security, 11 (2), pp. 74–83.
Keller, S.; Powell, A.; Horstmann, B.; Predmore, C.; Crawford, M. (2005). Information security Threats and practices in small businesses. Information Systems Management; Spring; 22.2 : pp. 7-19.
Kizza, J. (2005). Computer network security. Springer Science and Business Media; New York; 345 pp.
Montesino, R.; Fenz, S.; & Baluja, W. (2012). SIEM-based framework for security controls automation. Information Management & Computer Security; Vo. 20.4; pp. 248-263.
National Institute of Standards and Technology (2011). Five security best practices: Washington, D.C.
Rapkin, G. (2009). How to protect personally identifiable information: top ten data security best practices. Database and Network Journal. 39.1; Feb.: p19.
Schneier, B. (2000). Secrets & lies, Digital security in a networked worldJ. ohn Wiley, New York ; 275 pp.
Teta, S. & Athanasios, K. (2012). Inter-Sector Practices Reform for e-Government Integration Efficacy. Information Technology & People; 25.3: pp. 327-352.
Wilson, M. (2003). Network Security: Best Practices. Computerworld; Vol : Iss. Pp. 68.
- MLA Style
- APA Style
- Chicago Style
- Turabian
Ultius, Inc. "How Network Security Impacts Essay Writing Services." Ultius | Custom Writing and Editing Services. Ultius Blog, 06 Sep. 2019. https://www.ultius.com/ultius-blog/entry/how-network-security-impacts-essay-writing-services.html
Copied to clipboard
Click here for more help with MLA citations.
Ultius, Inc. (2019, September 06). How Network Security Impacts Essay Writing Services. Retrieved from Ultius | Custom Writing and Editing Services, https://www.ultius.com/ultius-blog/entry/how-network-security-impacts-essay-writing-services.html
Copied to clipboard
Click here for more help with APA citations.
Ultius, Inc. "How Network Security Impacts Essay Writing Services." Ultius | Custom Writing and Editing Services. September 06, 2019 https://www.ultius.com/ultius-blog/entry/how-network-security-impacts-essay-writing-services.html.
Copied to clipboard
Click here for more help with CMS citations.
Ultius, Inc. "How Network Security Impacts Essay Writing Services." Ultius | Custom Writing and Editing Services. September 06, 2019 https://www.ultius.com/ultius-blog/entry/how-network-security-impacts-essay-writing-services.html.
Copied to clipboard
Click here for more help with Turabian citations.